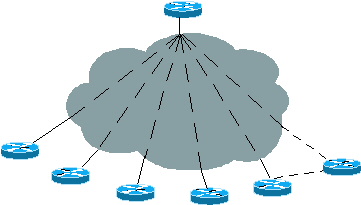
ODR (On Demand Routing) using CDP(Cisco Discovery Protocol) to send the prefixes of attached networks from stub networks to the hub or core router.The core router sends its interface address (of the shared link) as the default route for the stub router.The advantage is sending information such as prefix and mask and metric.This occurs every 60 seconds by default.This information populates the routing table of the core router and can be redistributed into a routing protocol.I added this picture to show you the meaning of the ODR.The top router is a core or hub router in which sends its shared link interface ip address as default router to the other routers called stub routers and know about those network:
 When working and configuring the ODR remember these:
When working and configuring the ODR remember these:
1. No ip routing protocols should be configured on the stub routers (Using default).
2. Any secondary ip address on the stub router are not propagated by CDP.
3. ODR must be configured on the core router.
4. CDP is enabled by default but for some WAN interfaces such as ATM you must enable it on the interface configuration command by cdp enable command.
5. Remember that CDP uses multicast.Therefore on WAN links you should using mapping method.
6. It might be necessary to tune the CDP timers to send updates in different interval than 60 seconds.
To configure CDP/ODR :
Router(config-if)#cd timer seconds
Router(config)#router odr --> only configured on the core/hub router
If you want more information or if my representaion is not friendly to you I've found the useful link on Cisco website, go and read more and better :
http://www.cisco.com/en/US/tech/tk365/technologies_q_and_a_item09186a0080093f1a.shtml
-------------
- Good Luck


