Thursday, August 10, 2006
Homeland Security: Fix your Windows
The agency, which also runs the United States Computer Emergency Readiness Team (US-CERT), sent out a news release on Wednesday recommending that people apply Microsoft's MS06-040 patch as quickly as possible. The software maker released the "critical" fix Tuesday as part of its monthly patch cycle.
"Users are encouraged to avoid delay in applying this security patch," the Department of Homeland Security said in the statement. The patch fixes a serious flaw that, if exploited, could enable an attacker to remotely take complete control of an affected system, the agency said.
Microsoft on Tuesday issued a dozen security bulletins, nine of which were tagged "critical," the company's highest severity rating. However, the flaw addressed in MS06-040 is the only one among the updates that could let an anonymous attacker remotely commandeer a Windows PC without any user interaction.
The flaw has some similarities to the Windows bug that enabled the notorious MSBlast worm to spread in 2003. Both security vulnerabilities are related to a Windows component called "remote procedure call," which provides support for networking features such as file sharing and printer sharing.
"Blaster took advantage of a vulnerability in the same service. We recognize that this is something that is easily exploitable," said Amol Sarwate, the manager of vulnerability research lab at Qualys. "It is excellent that DHS sent out this alert, because I think a lot of people are vulnerable."
Microsoft has seen a "very limited attack" that already used the newly disclosed flaw, the software maker said Tuesday.
Overnight, some hacker toolkits were updated with code that allows researchers to check for the flaw and exploit it, said Neel Mehta, a security expert at Internet Security Systems in Atlanta.
"This is a very serious vulnerability," Mehta said. "At the moment, this exploit is being used in targeted attacks to compromise specific systems. However, there is nothing about the nature of the vulnerability that prevents it from being used in a much more widespread fashion as part of a worm."
Microsoft worked with the Department of Homeland Security on the alert, a company representative said. "Microsoft...encourages customers to deploy this update on their systems as soon as possible, given that we are aware of targeted exploitation of the vulnerability," the representative said.
Microsoft deems the vulnerability critical for all versions of Windows. However, users of Windows XP with Service Pack 2 and Windows Server 2003 with Service Pack 1 should be protected by the Windows Firewall if they do not use file sharing and printer sharing, Christopher Budd, a security program manager at Microsoft, said in an interview Tuesday.
The Microsoft updates are available via the Windows Update and Automatic Updates tools as well as from Microsoft's Web site. Temporary workarounds are outlined in the security bulletins for those who can't immediately apply the patches.
By Joris Evers, CNET News.com
Published on ZDNet News: August 9, 2006, 10:37 AM PT
Sunday, July 09, 2006
launching interactive command-prompts on remote systems
Utilities like Telnet and remote control programs like Symantec's PC Anywhere let you execute programs on remote systems, but they can be a pain to set up and require that you install client software on the remote systems that you wish to access. PsExec is a light-weight telnet-replacement that lets you execute processes on other systems, complete with full interactivity for console applications, without having to manually install client software. PsExec's most powerful uses include launching interactive command-prompts on remote systems and remote-enabling tools like IpConfig that otherwise do not have the ability to show information about remote systems.
Download it from:
http://www.sysinternals.com/Files/PsExec.zip
Just copy PsExec onto your executable path. Typing "psexec" displays its usage syntax.
PsExec works on NT 4.0, Win2K, Windows XP and Server 2003 including x64 versions of Windows.
Do not use this as an abuse tool such as attack or so on if you read my blog as a technical man not voodoo.This is the only gift that you may give me.So good.
Saturday, July 08, 2006
Another security hole found in Excel
The flaw is due to a memory corruption error that occurs when handling or repairing a document containing overly long styles, the French Security Incident Response Team said in an advisory.
The flaw, which affects Excel 2000, 2002 and 2003 and Office 2000, XP and 2003, "could be exploited by attackers to execute arbitrary commands by convincing a user to open and repair a specially crafted Excel file," the advisory said.
A Microsoft representative said the company is investigating reports of a new vulnerability in Excel and was not aware of any attacks related to it.
"In order for this attack to be carried out, a user must first open a malicious Excel document that is sent as an e-mail attachment or otherwise provided to them by an attacker," the representative said in an e-mail. "Opening the Excel document out of e-mail will prompt the user to be careful about opening the attachment."
The vulnerability affects only users of Japanese, Korean or Chinese language versions of Excel, the Microsoft representative said.
Customers who believe they are affected can get more information on Microsoft's security Web site. For more information about protecting a computer from threats, Microsoft has this site.
Excel hackers have been busy. On June 16, experts warned about a hole that was exploited in at least one targeted cyberattack. About two weeks ago, an Excel hole was discovered that could crash the program after a malicious file is opened.
By Elinor Mills, CNET News.com
Published on ZDNet News: July 6, 2006, 6:15 PM PT
Tuesday, June 20, 2006
Send me your site/blog to link
If you want, you can send me your site or blog URL to link in my page.
----------------
Good Luck!
Sunday, June 18, 2006
Boot Speed-up Utility
BootVis Publisher's Description
Bootvis.exe is a performance tracing and visualization tool that Microsoft designed to help PC system designers and software developers identify performance issues for boot/resume timing while developing new PC products or supporting software.
Download it from:
http://www.soft32.com/download_19687.html
Windows XP Tips & Tricks - Part 3
The follow are some common Control Panel Applets that are located in the \windows\system32 directory.If you find yourself using any of these frequently, then you can simply make shortcuts to them on your desktop.
appwiz.cpl --> Add/Remove Programs
desk.cpl --> Display Properties
firewall.cpl --> Firewall Settings
inetcpl.cpl --> Internet Options
mmsys.cpl --> Sound and Audio
ncpa.cpl --> Network Connections
nusrmgr.cpl --> User Accounts
powercfg.cpl --> Power Options
sysdm.cpl --> System Properties
wscui.cpl --> Security Center
wuaucpl.cpl --> Automatic Updates Configuration
2. Windows Explorer Opens Search Companion Rather than the Folder:
If the Windows Explorer opens up the Search Companion rather than opening up the actual folder, the default setting for opening a folder is changed.
To correct this:
1. Start Regedit
2. Go to HKEY_CLASSES_ROOT \ Directory \ shell and HKEY_CLASSES_ROOT \ Drive \ shell]
3. Edit the default value to be explorer or none
3. System32 Folder Opens When Logging On:
If the System32 folder shows on the desktop, there may be an invalid entry in the Registry
1. Start Regedit
2. Go to both:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
3. Double check that the values do not have incorrect, incomplete, or blank entries
4. Not Viewing Zip Files as Folders:
If you want to turn of WindowsXP showing Zip files as folders,just run:
regsvr32 /u zipfldr.dll
5. Setting Capslock, Numlock, Scroll Lock:
If you want to set the startup state for any or all of these keys, you just need to edit the registry. 1. Start Regedit
2. Go to HKEY_CURRENT_USER \ Control Panel \ Keyboard
3. Open InitialKeyboardIndicators
4. Change the value to one of the following numbers
0 - All Keys off
1 - Caps Lock on
2 - Num Lock on
3 - Caps Lock and Num Lock on
4 - Scroll Lock on
5 - Caps Lock and Scroll Lock on
6 - Num Lock and Scroll Lock on
7 - Caps Lock, Num Lock, and Scroll Lock on
5. Log off and back on again
6. DOS Tips in XP:
Windows XP cmd tip (DOS isn’t dead... it just smells funny) Some command-line folder creation examples:
To create multiple folders at once, add them directly to the "md" command:
C:\> md this is a test
To create a folder several folders deep, use:
C:\> md this\is\a\test
Creating a folder with a long name requires the double-quote at the beginning:
C:\> md "this is a test
Bonus tip: Windows XP supports the forward slash "/" as a folder divider. Unix/Linux users: don't let the DOS environment get you down. Use a Unix-style CD command to change your present working directory:
C:\> cd Windows/system32/drivers/etc
Submitted by Bob and Tina
7. Restoring Desktop Icon to the Quicklaunch Bar:
If you mistakenly deleted the icon for the Desktop on the Quicklaunch toolbar
Go to C:\Documents and Settings\user_name\Application Data\Microsoft\Internet Explorer\Quick Launch(where user_name is replaced by your login name)
Create a Text file called ShowDesktop.SCF with the following contents:
[Shell
]Command=2
IconFile=explorer.exe,3
[Taskbar]Command=ToggleDesktop
8. Configure for Auto-Logon:
If you are the only person using the computer and what to have it automatically log you on,
1. Start / Run / "control userpasswords2" - no quotes
2. Uncheck User must enter a user name and password to use this computer
9. Disable Remembering Folder Settings:
If XP does not remember your folder settings, delete or rename the following registry keys:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\ShellNoRoam\BagMRU][HKEY_CURRENT_USER\Software\Microsoft\Windows\ShellNoRoam\Bags]
10. Disable Explorer Thumbnail View:
If you want disable the Explorer's ability to show the Thumbnail View:
1. Start Regedit
2. Go to HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Explorer \ Advanced 3. Change ClassicViewState to 1
11. Preventing Applications from Stealing the Focus:
To prevent applications from stealing the focus from the window you are working:
1. Start Regedit
2. Go to HKEY_CURRENT_USER \ Control Panel \ Desktop
3. Edit the key ForegroundLockTimeout
4. Give it a value of 00030d40
12. Disable Passport Pop-Up:
Normally, WindowsXP will prompt you 10 times that You Need a Passport to use WindowsXP Internet communication features.
To disable this:
1. Start Regedit
2. Go to HKEY_CURRENT_USER \ Software \ Microsoft \ MessengerService
3. Edit the binary key PassportBalloon
4. Give it a value of 0A (0A 00 00 00)
Saturday, June 17, 2006
Microsoft Excel Vulnerability
Last revised: --
Source: US-CERT
Systems Affected
* Microsoft Excel 2003
* Microsoft Excel XP (2002)
* Microsoft Excel for Mac
Microsoft Excel is included with Microsoft Office. Other versions of
Excel, and other Office programs may be affected or act as attack
vectors.
Overview
An unspecified vulnerability in Microsoft Excel could allow an
attacker to execute arbitrary code on a vulnerable system.
I. Description
Microsoft Excel contains an unspecified vulnerability. Opening a
specially crafted Excel document, including documents hosted on web
sites or attached to email messages, could trigger the vulnerability.
Office documents can contain embedded objects. For example, a
malicious Excel document could be embedded in an Word or PowerPoint
document. Office documents other than Excel documents could be used as
attack vectors.
For more information, please see Vulnerability Note VU#802324.
II. Impact
By convincing a user to open a specially crafted Excel document, an
attacker could execute arbitrary code on a vulnerable system. If the
user has administrative privileges, the attacker could gain complete
control of the system.
III. Solution
At the time of writing, there is no complete solution available.
Consider the following workarounds:
Do not open untrusted Excel documents
Do not open unfamiliar or unexpected Excel or other Office documents,
including those received as email attachments or hosted on a web site.
Please see Cyber Security Tip ST04-010 for more information.
Do not rely on file extension filtering
In most cases, Windows will call Excel to open a document even if the
document has an unknown file extension. For example, if document.x1s
(note the digit "1") contains the correct file header information,
Windows will open document.x1s with Excel.
Thursday, June 15, 2006
Windows XP Tips & Tricks - Part 2
If you want to rename multiple files in the same directory:
1. Using the Windows Explorer, select all the files you want to rename
2. Press F2 or right click and select Rename
3. Enter the prefix for the name you want
4. This will automatically rename the rest of the files Newname (1).jpg, Newname (2).jpg etc.
5. Make sure you include the extension if you have the Explorer configured to show them.
2. Speeding Up Network Browsing:
There are a lot of things which can negatively impact how fast XP will browse network shares. One has been previously covered regarding browsing to Win9x computers.
Other things you can try, especially when there is slow browsing to network shares with a lot of files:
1. Remove current shortcuts in My Network Places
2. Change the registry so shared folders on remote computers are not automatically added to My Network Places when you even open a document from that shared folder
1. Start Regedit
2. Create a DWORD value:
3. HKEY_Current_User \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer \ NoRecentDocsNetHood to 1.
4. I have also seen setting the following help as well.HKEY_Current_User \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer \ UseDesktopIniCache to 1.
3. Increase the amount of data is buffered at one time to send to a client. On the computer with the shared directory:
1. Start Regedit
2. Go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
3. Create a DWORD Key called SizReqBuf
4. Give it a value of Hex FFFF
3. Make Pictures Smaller Unavailable:
When you try and send pictures through e-mail, you should normally be given the option to make them smaller. If this option is not available, a DLL file may need to be registered.
1. Start
2. Run
3. regsvr32 shimgvw.dll
4. Creating a Suspend Shortcut:
If you would like to create an icon to suspend your computer,
1. Right click on the Desktop
2. New / Shortcut
3. Enter in rundll32.exe PowrProf.dll, SetSuspendState
4. Give it whatever name you want
Now when you click on that shortcut, your computer will shutdown and suspend
5. Determining Which Services are Associated with SVCHOST:
Since so many critical services are run with each svchost,You can see which ones are being used by opening a cmd prompt and running:
tasklist /svc /fi "imagename eq svchost.exe"
Note: This is available only with XP Pro
6. Identify Faulty Device Drivers:
If you are having problems with lockups, blue screens, or can only get to safe mode,often the problem is due to a faulty device driver.
One way to help identify them is through the use of the Verfier program
1. Start / Run / Verifier
2. Keep the default of Create Standard Settings
3. Select the type of drivers you want to confirm
4. A list of drivers to be verified on the next boot will be shown.
5. Reboot
6. If your computer stops with a blue screen, you should get an error message with the problem driver
7. To turn off the Verifier, run verifier /reset
7. Viewing Installed Drivers
If you want to see a list of installed drivers, you can run the driverquery programThere are a lot of available switches to view different types of information.On use can be to export to a CSV file for viewing in ExcelAn example would then be:
Driverquery /v /fo csv > drivers.csv
8. Guest Only Network Access
If you try and connect to an XP computer and are shown a logins screen with only the computername/Guest,You may need to change one of the Local Security Policies:
1. Got to Control Panel - Administrative Tools
2. Go to Local Policies - Security Options
3. Check teh Network access: Sharing and security model for local accounts
4. Set it to Classic - local users authenticate as themselves
9. Not Displaying Previous Network Share Shortcuts:
By default, when you go to Network Places, it will scan and show shortcuts to previous network shares.To turn this off and remove any current shortcuts
1. Open up the Windows Explorer
2. Go to Tools / Folder Options / View
3. The top section should be Files and Folders
4. Uncheck Automatically search for network folders and printers
5. Then go into Network Neighborhood Select all the previous netowork connections Delete them
Next time you look at the Network Neighborhood, they should not repopulate
10. Hiding a XP Computer from Network Neighborhood:
If you want to share files from a XP computer, yet want to remove it from showing up in the Network Neighborhood,
Run net config server /hidden:yes
--------------
Good Luck!
Wednesday, June 14, 2006
Windows XP Tips & Tricks - Part 1
WindowsXP has a new feature called Prefetch. This keeps a shortcut to recently used programs. However it can fill up with old and obsolete programs.
To clean this periodically go to:
1. Star / Run / Prefetch.
2. Press Ctrl-A to highlight all the files.
3. Delete them.
2. Not Displaying Logon, Logoff, Startup and Shutdown Status Messages:
1. Start Regedit.
2. Go to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system 3. If it is not already there, create a DWORD value named DisableStatusMessages.
4. Give it a value of 1.
3. Bringing Up the Shutdown Dialog Box:
1. Create a new txt file somewhere on your system, open it and put in this one line: (newActiveXObject("Shell.Application")).ShutdownWindows();
2. Save and Close the file. Change the extension to js and your got it.
3. You can make a shortcut to that file to make it easy to shut down your system.
4. Increasing the Folder Cache:
The default setting for WindowsXP is to cache the Explorer settings for 400 folders.To increase it:
1. Start Regedit.
2. Go to HKEY_CURRENT_USER\Software\Microsoft\Windows\ShellNoRoam.
3. Change the vaule of BagMRU to whatever size you want (hex).
1000 - 3e8
2000 - 7d0
3000 - bb8
4000 - fa0
5000 - 1388
5. Poweroff at Shutdown:
If your computer does not turn off the power when doing a shutdown,you may need to edit the registry. I have all the correct BIOS and Power settings and still needed to do this.
1. Start Regedit.
2. Go to HKEY_CURRENT_USER\Control Panel\Desktop.
3. Edit the key PowerOffActive and give it a value of 1.
4. You can do the same in HKEY_USERS\.DEFAULT\Control Panel\Desktop.
6. Show Hidden Devices:
You can show hidden devices in the Device Manager. One way is by making a simple registry change. The other is through a batch file.
Registry Change:
1. Go to HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet001 \ Control \ Session Manager \ Environment.
2. Create a string DEVMGR_SHOW_NONPRESENT_DEVICES.
3. Give it a value of 1.
Batch File
@Echo Off
Prompt $p$g
set DEVMGR_SHOW_NONPRESENT_DEVICES=1
start devmgmt.msc
exit
7. Disable Shared Documents:
To disable the Shared Documents folder that shows up on the network:
1. Start Regedit.
2. Go to HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer 3. Create a new DWORD Value.
4. Give it the name NoSharedDocuments.
5. Give it a value of 1.
6. Log off or reboot.
------------
Good Luck!
Saturday, June 10, 2006
ODR - On Demand Routing
ODR (On Demand Routing) using CDP(Cisco Discovery Protocol) to send the prefixes of attached networks from stub networks to the hub or core router.The core router sends its interface address (of the shared link) as the default route for the stub router.The advantage is sending information such as prefix and mask and metric.This occurs every 60 seconds by default.This information populates the routing table of the core router and can be redistributed into a routing protocol.I added this picture to show you the meaning of the ODR.The top router is a core or hub router in which sends its shared link interface ip address as default router to the other routers called stub routers and know about those network:
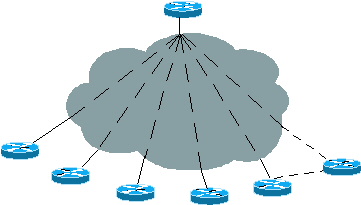 When working and configuring the ODR remember these:
When working and configuring the ODR remember these:
1. No ip routing protocols should be configured on the stub routers (Using default).
2. Any secondary ip address on the stub router are not propagated by CDP.
3. ODR must be configured on the core router.
4. CDP is enabled by default but for some WAN interfaces such as ATM you must enable it on the interface configuration command by cdp enable command.
5. Remember that CDP uses multicast.Therefore on WAN links you should using mapping method.
6. It might be necessary to tune the CDP timers to send updates in different interval than 60 seconds.
To configure CDP/ODR :
Router(config-if)#cd timer seconds
Router(config)#router odr --> only configured on the core/hub router
If you want more information or if my representaion is not friendly to you I've found the useful link on Cisco website, go and read more and better :
http://www.cisco.com/en/US/tech/tk365/technologies_q_and_a_item09186a0080093f1a.shtml
-------------
- Good Luck
Thursday, May 25, 2006
Microsoft advises 'safe mode' for Word
In the wake of at least one targeted attack that exploits a new flaw in Word, Microsoft is advising users to run the application in "safe mode."
Running Word in the restricted mode will not fix the vulnerability, but it will help block known modes of attack, Microsoft said in a security advisory published late Monday. The software maker is also developing a security update for Word, which should be available on June 13 or sooner, as warranted, the company said.
Enabling "safe mode" is a two-step process. The first part involves disabling the use of Word as an e-mail client, the second is appending "/safe" to the command line that starts Word. Microsoft provides instructions for home and enterprise users in its security advisory.
News of the Word flaw and attack surfaced last week. Word 2002 and Word 2003 are vulnerable, but Word 2000 is not, Microsoft said. For an attack to be carried out, a PC user must open a malicious Word document sent in an e-mail or otherwise provided by an attacker, it said.
Aside from changing the way Word runs, people can protect their systems by being careful in the opening of Word documents received as an unexpected e-mail attachment, Microsoft said.
Source:By Joris Evers, CNET News.com
Published on ZDNet News: May 23, 2006, 4:25 PM PT
Saturday, January 14, 2006
Apple QuickTime Vulnerabilities
Original release date: January 11, 2006
Last revised: January 11, 2006
Source: US-CERT
Systems Affected
Apple QuickTime on systems running
* Apple Mac OS X
* Microsoft Windows XP
* Microsoft Windows 2000
Overview
Apple has released QuickTime 7.0.4 to correct multiple
vulnerabilities. The impacts of these vulnerabilities include
execution of arbitrary code and denial of service.
I. Description
Apple QuickTime 7.0.4 resolves a number of image and media file
handling vulnerabilities. Further details are available in the
following Vulnerability Notes:
VU#629845 - Apple QuickTime image handling buffer overflow
Apple QuickTime contains a heap overflow vulnerability that may allow
an attacker to execute arbitrary code or cause a denial-of-service
condition.
(CAN-2005-2340)
VU#921193 - Apple QuickTime fails to properly handle corrupt media
files
Apple QuickTime contains a heap overflow vulnerability in the handling
of media files. This vulnerability may allow a remote, unauthenticated
attacker to execute arbitrary code or cause a denial of service on a
vulnerable system.
(CAN-2005-4092)
VU#115729 - Apple QuickTime fails to properly handle corrupt TGA
images
A flaw in the way Apple QuickTime handles Targa (TGA) image format
files could allow a remote attacker to execute arbitrary code on a
vulnerable system.
(CAN-2005-3707)
VU#150753 - Apple QuickTime fails to properly handle corrupt TIFF
images
Apple QuickTime contains an integer overflow vulnerability in the
handling of TIFF images. This vulnerability may allow a remote,
unauthenticated attacker to execute arbitrary code or cause a denial
of service on a vulnerable system.
(CAN-2005-3710)
VU#913449 - Apple QuickTime fails to properly handle corrupt GIF
images
A flaw in the way Apple QuickTime handles Graphics Interchange Format
(GIF) files could allow a remote attacker to execute arbitrary code on
a vulnerable system.
(CAN-2005-3713)
II. Impact
The impacts of these vulnerabilities vary. For information about
specific impacts, please see the Vulnerability Notes. Potential
consequences include remote execution of arbitrary code or commands
and denial of service.
III. Solution
Upgrade
Upgrade to QuickTime 7.0.4.
Microsoft Windows, Outlook, and Exchange Vulnerabilities
Original release date: January 10, 2006
Last revised: January 10, 2006
Source: US-CERT
Systems Affected
* Microsoft Windows
* Microsoft Outlook
* Microsoft Exchange
For more complete information, refer to the Microsoft Security
Bulletin Summary for January 2006.
Overview
Microsoft has released updates that address critical vulnerabilities
in Windows, Outlook, and Exchange. Exploitation of these
vulnerabilities could allow a remote, unauthenticated attacker to
execute arbitrary code or cause a denial of service on a vulnerable
system.
I. Description
Microsoft Security Bulletins for January 2006 address vulnerabilities
in Microsoft Windows, Outlook, and Exchange. Further information is
available in the following US-CERT Vulnerability Notes:
VU#915930 - Microsoft embedded web font buffer overflow
A heap-based buffer overflow in the way Microsoft Windows processes
embedded web fonts may allow a remote, unauthenticated attacker to
execute arbitrary code on a vulnerable system.
(CVE-2006-0010)
VU#252146 - Microsoft Outlook and Microsoft Exchange TNEF decoding
vulnerability
Microsoft Outlook and Microsoft Exchange contain an unspecified
vulnerability in processing TNEF attachments. This may allow a remote,
unauthenticated attacker to execute arbitrary code on a system running
the vulnerable software.
(CVE-2006-0002)
II. Impact
Exploitation of these vulnerabilities may allow a remote,
unauthenticated attacker to execute arbitrary code with the privileges
of the user. If the user is logged on with administrative privileges,
the attacker could take complete control of an affected system. An
attacker may also be able to cause a denial of service.
III. Solution
Apply Updates
Microsoft has provided the updates for these vulnerabilities in the
Security Bulletins and on the Microsoft Update site.
Monday, January 09, 2006
My Guestbook Signing
Note: The link for my Guestbook is available on my page, too.
Major Internet Backbones
In this topic, I tell you major internet backbones...
* At the first time lets know the meaning of the backbone:
Before reading, you have to know:
DS0 is a 64 kilobits per second link (I called it basic rate).
T1 line is a 1.544 megabits per second link (24 DS0 lines).
T3 line is a 43.232 megabits per second link (28 T1s or ).
OC3 is a 155 megabits per second link (84 T1s).
OC12 is a 622 megabits per second link (4 OC3s).
OC48 is a 2.5 gigabits per seconds link (4 OC12s).
OC192 is a 9.6 gigabits per second link (4 OC48s).
The National Science Foundation (NSF) created the first high-speed backbone in 1987. Called NSFNET, it was a T1 line that connected 170 smaller networks together and operated at 1.544 Mbps (million bits per second). IBM, MCI and Merit worked with NSF to create the backbone and developed a T3 (45 Mbps) backbone the following year.
Backbones are typically fiber optic trunk lines. The trunk line has multiple fiber optic cables combined together to increase the capacity. Fiber optic cables are designated OC for optical carrier, such as OC-3, OC-12 or OC-48. An OC-3 line is capable of transmitting 155 Mbps while an OC-48 can transmit 2,488 Mbps (2.488 Gbps). Compare that to a typical 56K modem transmitting 56,000 bps and you see just how fast a modern backbone is.
Today there are many companies that operate their own high-capacity backbones, and all of them interconnect at various NAPs around the world. In this way, everyone on the Internet, no matter where they are and what company they use, is able to talk to everyone else on the planet. The entire Internet is a gigantic, sprawling agreement between companies to intercommunicate freely.
** Major Internet Backbones (Sorted by "connectivity"):
AS 701 - UUNET/WorldCom/MCI
AS 1239 - Sprint
AS 3561 - Cable & Wireless
USA AS 1 - Genuity (Also known as Level 3)
AS 6461 - AboveNet
AS 7018 - AT&T
AS 209 - Qwest
AS 2914 - Verio
AS 3549 - Global Crossing
AS 6453 - TeleGlobe
AS 702 - UUNET (also first)
AS 2548- Intermedia
AS 6347 - Savvis
AS 1755 - Ebone
AS 4648 - Netgate (Exchange Point: New Zealand)
AS 174 - PSINet (cogent)
AS 5459 - LINX (Exchange Point: London)
AS 8918 - Carrier1 (bankrupt) (netherlands portion)
AS 3300 - Infonet (Their European network)
AS 703 - UUNET/WorldCom/MCI (also first)
AS 3967 - Exodus (now with Cable & Wireless)
AS 8297 - Teleglobe
AS 5673 - Pacific Bell
AS 2828 - Concentric (now with XO)
AS 4000 - Sprint (Also listed at number 2)
AS 4200 - AGIS (telia)
AS7474 - optus (Australia)
AS 4766 - KIX (Exchange Point: Korea)
AS 3786 - DACOM ( map from KIDC)
AS 5519 - XO Communication
AS 286 - EUNET (KPN)
AS 8342 - ROSTELECOM
Update for Microsoft Windows Metafile Vulnerability
Last revised: --
Source: US-CERT
Systems Affected
* Systems running Microsoft Windows
Overview
Microsoft Security Bulletin MS06-001 contains an update to fix a
vulnerability in the way Microsoft Windows handles images in the
Windows Metafile (WMF) format.
I. Description
TA05-362A describes a vulnerability in the way Microsoft Windows
handles Windows Metafile images. This vulnerability could allow a
remote attacker to execute arbitrary code. Microsoft Security Bulletin
MS06-001 contains an update to fix this vulnerability.
The vulnerability is described in further detail in VU#181038.
II. Impact
A remote, unauthenticated attacker may be able to execute arbitrary
code if the user is persuaded to view a specially crafted Windows
Metafile.
III. Solution
Apply a patch from your vendor
Install the appropriate update according to Microsoft Security
Bulletin MS06-001.