Saturday, June 17, 2006
Microsoft Excel Vulnerability
Last revised: --
Source: US-CERT
Systems Affected
* Microsoft Excel 2003
* Microsoft Excel XP (2002)
* Microsoft Excel for Mac
Microsoft Excel is included with Microsoft Office. Other versions of
Excel, and other Office programs may be affected or act as attack
vectors.
Overview
An unspecified vulnerability in Microsoft Excel could allow an
attacker to execute arbitrary code on a vulnerable system.
I. Description
Microsoft Excel contains an unspecified vulnerability. Opening a
specially crafted Excel document, including documents hosted on web
sites or attached to email messages, could trigger the vulnerability.
Office documents can contain embedded objects. For example, a
malicious Excel document could be embedded in an Word or PowerPoint
document. Office documents other than Excel documents could be used as
attack vectors.
For more information, please see Vulnerability Note VU#802324.
II. Impact
By convincing a user to open a specially crafted Excel document, an
attacker could execute arbitrary code on a vulnerable system. If the
user has administrative privileges, the attacker could gain complete
control of the system.
III. Solution
At the time of writing, there is no complete solution available.
Consider the following workarounds:
Do not open untrusted Excel documents
Do not open unfamiliar or unexpected Excel or other Office documents,
including those received as email attachments or hosted on a web site.
Please see Cyber Security Tip ST04-010 for more information.
Do not rely on file extension filtering
In most cases, Windows will call Excel to open a document even if the
document has an unknown file extension. For example, if document.x1s
(note the digit "1") contains the correct file header information,
Windows will open document.x1s with Excel.
Thursday, June 15, 2006
Windows XP Tips & Tricks - Part 2
If you want to rename multiple files in the same directory:
1. Using the Windows Explorer, select all the files you want to rename
2. Press F2 or right click and select Rename
3. Enter the prefix for the name you want
4. This will automatically rename the rest of the files Newname (1).jpg, Newname (2).jpg etc.
5. Make sure you include the extension if you have the Explorer configured to show them.
2. Speeding Up Network Browsing:
There are a lot of things which can negatively impact how fast XP will browse network shares. One has been previously covered regarding browsing to Win9x computers.
Other things you can try, especially when there is slow browsing to network shares with a lot of files:
1. Remove current shortcuts in My Network Places
2. Change the registry so shared folders on remote computers are not automatically added to My Network Places when you even open a document from that shared folder
1. Start Regedit
2. Create a DWORD value:
3. HKEY_Current_User \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer \ NoRecentDocsNetHood to 1.
4. I have also seen setting the following help as well.HKEY_Current_User \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer \ UseDesktopIniCache to 1.
3. Increase the amount of data is buffered at one time to send to a client. On the computer with the shared directory:
1. Start Regedit
2. Go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
3. Create a DWORD Key called SizReqBuf
4. Give it a value of Hex FFFF
3. Make Pictures Smaller Unavailable:
When you try and send pictures through e-mail, you should normally be given the option to make them smaller. If this option is not available, a DLL file may need to be registered.
1. Start
2. Run
3. regsvr32 shimgvw.dll
4. Creating a Suspend Shortcut:
If you would like to create an icon to suspend your computer,
1. Right click on the Desktop
2. New / Shortcut
3. Enter in rundll32.exe PowrProf.dll, SetSuspendState
4. Give it whatever name you want
Now when you click on that shortcut, your computer will shutdown and suspend
5. Determining Which Services are Associated with SVCHOST:
Since so many critical services are run with each svchost,You can see which ones are being used by opening a cmd prompt and running:
tasklist /svc /fi "imagename eq svchost.exe"
Note: This is available only with XP Pro
6. Identify Faulty Device Drivers:
If you are having problems with lockups, blue screens, or can only get to safe mode,often the problem is due to a faulty device driver.
One way to help identify them is through the use of the Verfier program
1. Start / Run / Verifier
2. Keep the default of Create Standard Settings
3. Select the type of drivers you want to confirm
4. A list of drivers to be verified on the next boot will be shown.
5. Reboot
6. If your computer stops with a blue screen, you should get an error message with the problem driver
7. To turn off the Verifier, run verifier /reset
7. Viewing Installed Drivers
If you want to see a list of installed drivers, you can run the driverquery programThere are a lot of available switches to view different types of information.On use can be to export to a CSV file for viewing in ExcelAn example would then be:
Driverquery /v /fo csv > drivers.csv
8. Guest Only Network Access
If you try and connect to an XP computer and are shown a logins screen with only the computername/Guest,You may need to change one of the Local Security Policies:
1. Got to Control Panel - Administrative Tools
2. Go to Local Policies - Security Options
3. Check teh Network access: Sharing and security model for local accounts
4. Set it to Classic - local users authenticate as themselves
9. Not Displaying Previous Network Share Shortcuts:
By default, when you go to Network Places, it will scan and show shortcuts to previous network shares.To turn this off and remove any current shortcuts
1. Open up the Windows Explorer
2. Go to Tools / Folder Options / View
3. The top section should be Files and Folders
4. Uncheck Automatically search for network folders and printers
5. Then go into Network Neighborhood Select all the previous netowork connections Delete them
Next time you look at the Network Neighborhood, they should not repopulate
10. Hiding a XP Computer from Network Neighborhood:
If you want to share files from a XP computer, yet want to remove it from showing up in the Network Neighborhood,
Run net config server /hidden:yes
--------------
Good Luck!
Wednesday, June 14, 2006
Windows XP Tips & Tricks - Part 1
WindowsXP has a new feature called Prefetch. This keeps a shortcut to recently used programs. However it can fill up with old and obsolete programs.
To clean this periodically go to:
1. Star / Run / Prefetch.
2. Press Ctrl-A to highlight all the files.
3. Delete them.
2. Not Displaying Logon, Logoff, Startup and Shutdown Status Messages:
1. Start Regedit.
2. Go to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system 3. If it is not already there, create a DWORD value named DisableStatusMessages.
4. Give it a value of 1.
3. Bringing Up the Shutdown Dialog Box:
1. Create a new txt file somewhere on your system, open it and put in this one line: (newActiveXObject("Shell.Application")).ShutdownWindows();
2. Save and Close the file. Change the extension to js and your got it.
3. You can make a shortcut to that file to make it easy to shut down your system.
4. Increasing the Folder Cache:
The default setting for WindowsXP is to cache the Explorer settings for 400 folders.To increase it:
1. Start Regedit.
2. Go to HKEY_CURRENT_USER\Software\Microsoft\Windows\ShellNoRoam.
3. Change the vaule of BagMRU to whatever size you want (hex).
1000 - 3e8
2000 - 7d0
3000 - bb8
4000 - fa0
5000 - 1388
5. Poweroff at Shutdown:
If your computer does not turn off the power when doing a shutdown,you may need to edit the registry. I have all the correct BIOS and Power settings and still needed to do this.
1. Start Regedit.
2. Go to HKEY_CURRENT_USER\Control Panel\Desktop.
3. Edit the key PowerOffActive and give it a value of 1.
4. You can do the same in HKEY_USERS\.DEFAULT\Control Panel\Desktop.
6. Show Hidden Devices:
You can show hidden devices in the Device Manager. One way is by making a simple registry change. The other is through a batch file.
Registry Change:
1. Go to HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet001 \ Control \ Session Manager \ Environment.
2. Create a string DEVMGR_SHOW_NONPRESENT_DEVICES.
3. Give it a value of 1.
Batch File
@Echo Off
Prompt $p$g
set DEVMGR_SHOW_NONPRESENT_DEVICES=1
start devmgmt.msc
exit
7. Disable Shared Documents:
To disable the Shared Documents folder that shows up on the network:
1. Start Regedit.
2. Go to HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer 3. Create a new DWORD Value.
4. Give it the name NoSharedDocuments.
5. Give it a value of 1.
6. Log off or reboot.
------------
Good Luck!
Saturday, June 10, 2006
ODR - On Demand Routing
ODR (On Demand Routing) using CDP(Cisco Discovery Protocol) to send the prefixes of attached networks from stub networks to the hub or core router.The core router sends its interface address (of the shared link) as the default route for the stub router.The advantage is sending information such as prefix and mask and metric.This occurs every 60 seconds by default.This information populates the routing table of the core router and can be redistributed into a routing protocol.I added this picture to show you the meaning of the ODR.The top router is a core or hub router in which sends its shared link interface ip address as default router to the other routers called stub routers and know about those network:
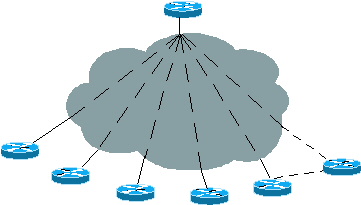 When working and configuring the ODR remember these:
When working and configuring the ODR remember these:
1. No ip routing protocols should be configured on the stub routers (Using default).
2. Any secondary ip address on the stub router are not propagated by CDP.
3. ODR must be configured on the core router.
4. CDP is enabled by default but for some WAN interfaces such as ATM you must enable it on the interface configuration command by cdp enable command.
5. Remember that CDP uses multicast.Therefore on WAN links you should using mapping method.
6. It might be necessary to tune the CDP timers to send updates in different interval than 60 seconds.
To configure CDP/ODR :
Router(config-if)#cd timer seconds
Router(config)#router odr --> only configured on the core/hub router
If you want more information or if my representaion is not friendly to you I've found the useful link on Cisco website, go and read more and better :
http://www.cisco.com/en/US/tech/tk365/technologies_q_and_a_item09186a0080093f1a.shtml
-------------
- Good Luck
Thursday, May 25, 2006
Microsoft advises 'safe mode' for Word
In the wake of at least one targeted attack that exploits a new flaw in Word, Microsoft is advising users to run the application in "safe mode."
Running Word in the restricted mode will not fix the vulnerability, but it will help block known modes of attack, Microsoft said in a security advisory published late Monday. The software maker is also developing a security update for Word, which should be available on June 13 or sooner, as warranted, the company said.
Enabling "safe mode" is a two-step process. The first part involves disabling the use of Word as an e-mail client, the second is appending "/safe" to the command line that starts Word. Microsoft provides instructions for home and enterprise users in its security advisory.
News of the Word flaw and attack surfaced last week. Word 2002 and Word 2003 are vulnerable, but Word 2000 is not, Microsoft said. For an attack to be carried out, a PC user must open a malicious Word document sent in an e-mail or otherwise provided by an attacker, it said.
Aside from changing the way Word runs, people can protect their systems by being careful in the opening of Word documents received as an unexpected e-mail attachment, Microsoft said.
Source:By Joris Evers, CNET News.com
Published on ZDNet News: May 23, 2006, 4:25 PM PT
Saturday, January 14, 2006
Apple QuickTime Vulnerabilities
Original release date: January 11, 2006
Last revised: January 11, 2006
Source: US-CERT
Systems Affected
Apple QuickTime on systems running
* Apple Mac OS X
* Microsoft Windows XP
* Microsoft Windows 2000
Overview
Apple has released QuickTime 7.0.4 to correct multiple
vulnerabilities. The impacts of these vulnerabilities include
execution of arbitrary code and denial of service.
I. Description
Apple QuickTime 7.0.4 resolves a number of image and media file
handling vulnerabilities. Further details are available in the
following Vulnerability Notes:
VU#629845 - Apple QuickTime image handling buffer overflow
Apple QuickTime contains a heap overflow vulnerability that may allow
an attacker to execute arbitrary code or cause a denial-of-service
condition.
(CAN-2005-2340)
VU#921193 - Apple QuickTime fails to properly handle corrupt media
files
Apple QuickTime contains a heap overflow vulnerability in the handling
of media files. This vulnerability may allow a remote, unauthenticated
attacker to execute arbitrary code or cause a denial of service on a
vulnerable system.
(CAN-2005-4092)
VU#115729 - Apple QuickTime fails to properly handle corrupt TGA
images
A flaw in the way Apple QuickTime handles Targa (TGA) image format
files could allow a remote attacker to execute arbitrary code on a
vulnerable system.
(CAN-2005-3707)
VU#150753 - Apple QuickTime fails to properly handle corrupt TIFF
images
Apple QuickTime contains an integer overflow vulnerability in the
handling of TIFF images. This vulnerability may allow a remote,
unauthenticated attacker to execute arbitrary code or cause a denial
of service on a vulnerable system.
(CAN-2005-3710)
VU#913449 - Apple QuickTime fails to properly handle corrupt GIF
images
A flaw in the way Apple QuickTime handles Graphics Interchange Format
(GIF) files could allow a remote attacker to execute arbitrary code on
a vulnerable system.
(CAN-2005-3713)
II. Impact
The impacts of these vulnerabilities vary. For information about
specific impacts, please see the Vulnerability Notes. Potential
consequences include remote execution of arbitrary code or commands
and denial of service.
III. Solution
Upgrade
Upgrade to QuickTime 7.0.4.
Microsoft Windows, Outlook, and Exchange Vulnerabilities
Original release date: January 10, 2006
Last revised: January 10, 2006
Source: US-CERT
Systems Affected
* Microsoft Windows
* Microsoft Outlook
* Microsoft Exchange
For more complete information, refer to the Microsoft Security
Bulletin Summary for January 2006.
Overview
Microsoft has released updates that address critical vulnerabilities
in Windows, Outlook, and Exchange. Exploitation of these
vulnerabilities could allow a remote, unauthenticated attacker to
execute arbitrary code or cause a denial of service on a vulnerable
system.
I. Description
Microsoft Security Bulletins for January 2006 address vulnerabilities
in Microsoft Windows, Outlook, and Exchange. Further information is
available in the following US-CERT Vulnerability Notes:
VU#915930 - Microsoft embedded web font buffer overflow
A heap-based buffer overflow in the way Microsoft Windows processes
embedded web fonts may allow a remote, unauthenticated attacker to
execute arbitrary code on a vulnerable system.
(CVE-2006-0010)
VU#252146 - Microsoft Outlook and Microsoft Exchange TNEF decoding
vulnerability
Microsoft Outlook and Microsoft Exchange contain an unspecified
vulnerability in processing TNEF attachments. This may allow a remote,
unauthenticated attacker to execute arbitrary code on a system running
the vulnerable software.
(CVE-2006-0002)
II. Impact
Exploitation of these vulnerabilities may allow a remote,
unauthenticated attacker to execute arbitrary code with the privileges
of the user. If the user is logged on with administrative privileges,
the attacker could take complete control of an affected system. An
attacker may also be able to cause a denial of service.
III. Solution
Apply Updates
Microsoft has provided the updates for these vulnerabilities in the
Security Bulletins and on the Microsoft Update site.


